How to Scan SCTP Ports with Nmap (Step-by-Step Guide)

SCTP scan is a focused Nmap method for locating SCTP-enabled hosts and open SCTP ports. These ports are commonly used in SIGTRAN/SS7 deployments. Because SCTP appears in many telecom core networks, accurate scanning is vital for pentesters assessing signaling surfaces. This article provides practical Nmap commands, example outputs, and guidance on safe lab setups. You can reproduce these tests without impacting live systems. If you need a test machine, an Eldernode Linux VPS is a convenient option.
What is SCTP INIT Scan?
SCTP is an alternative to the TCP and UDP protocols. It combines most characteristics of TCP and UDP and also adds new features like multi-homing and multi-streaming. SCTP’s INIT scan is a half-open probe similar to TCP SYN scanning.
Since you don’t open a full SCTP association, this technique is known as half-open scanning. You send an INIT chunk as if you are going to open a real association. Then wait for a response.
There is lots of room for improvement in the SCTP scan. Let’s review some of them:
– Complete implementation using libpcap
– Identification of scan response packet
– Better parameter checking
SCTP Scanning and its Applications
SCTP is organized with TCP or UDP ports and the address space of SCTP ports is 16 bits. There are 65536 ports (from 0 to 65535). The main goal of the SCTP scan is to find SCTP live machines and open ports. SCTP scan embeds a list of common SCTP ports. It does this to find them by not scanning the 65535 ports but a smaller subset. SCTP scan enables you to do many things such as:
1- Scan a single port on a machine
2- Scan whole A, B, C networks for machines with SCTP stacks
3- Scan for frequent ports on individual machine or whole networks
4- fuzz SCTP stacks on one host
5- Port scan a host for the whole 65535 ports
6- Start a dummy server that binds socket 1000 which can be later scanned
Also, there is some handy option that enables SCTP scan to automatically portscan a machine as soon as it finds that this host actually supports SCTP.
Scan Ports With SCTP On Nmap
You can use SCTP packets to determine if a host is online by sending SCTP INIT packets and looking for ABORT or INIT ACK responses. This technique is named SCTP INIT ping scan that is implemented by Nmap.
However, to scan a port with SCTP, first, open your terminal and run:
nmap -sn -PY <target>
Then, you can view the output that is the same format as the other types of ping scans:
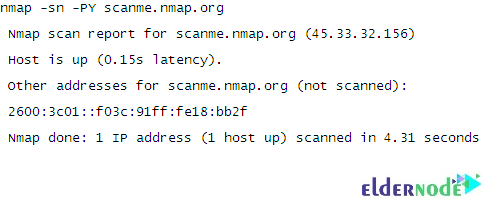
You should view the output as shown in the above image. The arguments -sn -PY scanme.nmap.org tell Nmap to scan an SCTP INIT going scan against the host scanme.nmap.org. This determines if it is online.
Conclusion
Scanning SCTP with Nmap isn’t something you’ll do every day. However, when you’re working around telecom or SIGTRAN traffic it becomes really useful. The commands we went through should give you a solid starting point. Also, the examples show what to expect in real output. Just make sure you only test systems you’re allowed to. The safest way is to play around in a lab setup or fire up a VPS where nothing critical is at risk.