
[Updated] Kali Linux is a Debian-based Linux distribution. It is a specially designed OS for network analysts and Penetration testers. Due to the open-source operating system, the operating system has many extensions and versions, each of which is designed and developed for a specific purpose and purpose. One of these versions, which is particularly useful for hacking and security and is a powerful operating system, is the Kali Linux operating system. This tutorial presents Introduction Kali Linux Server And Its Applications. Choose a perfect package on Eldernode to purchase your own Linux VPS.
Table of Contents
Introduction to Kali Linux Server
What is Kali Linux?
So far, hundreds of different distributions for Linux have been provided by individuals and companies. Each of these distributions has its own characteristics. Operating systems like Ubuntu, OpenSUSE, Fedora, BackTrack, and many more. We will focus more on the Kali Linux operating system. As we mentioned, Kali is a Linux distribution specifically geared towards professional penetration testers and security specialists. So, if you are unfamiliar with Linux, Kali Linux is Not a recommended distribution.
Kali Linux Advantages
Kali Linux is great for those who are intermediate in Linux and have their hands on Linux commands. Let’s review the advantages of this most advanced Penetration testing distribution:
1- More than 600 Penetration testing and network security tools pre-installed.
2- Completely free and open source.
3- It supports many languages.
4- Could be easily used with Rasberry Pi.
5- Wide-ranging wireless device support
Kali Linux Disadvantages
Maybe the most disadvantage of Kali Linux is that it is not recommending for those who are new to Linux and want to learn Linux. Here are some others:
1- It is a bit slower.
2- Some software may malfunction.
Most Powerful Hack and Intrusion Tool
The operating system is designing and developing to perform intrusion testing and vulnerability detection of various types of computer systems. Prior to Kali Linux, security professionals and hackers used Linux backups to perform their tests and intrusions. But with the introduction of Kali Linux, most people migrated to it and somehow replaced Kali Linux with the backtrack.
The Kali Linux operating system includes hundreds of different tools for performing security tests and intrusions into computer systems. Each of these tools has high power and special features.
This powerful operating system has a very high penetration capability. Anyone working in the field of hacking and security should be familiar with this operating system and its various tools. In fact, Kali Linux has been a great tool for hackers to easily access other systems, and for security professionals to identify and work around vulnerabilities.
Various Kali Linux Hack Tools
As mentioned, the Kali Linux operating system has more than 600 permeability testing and hack tools. Some of these tools are extremely powerful in penetration and can easily handle complex intrusions with very little programming knowledge. However, Kali Linux provides people with the tool and people can use it with their knowledge.
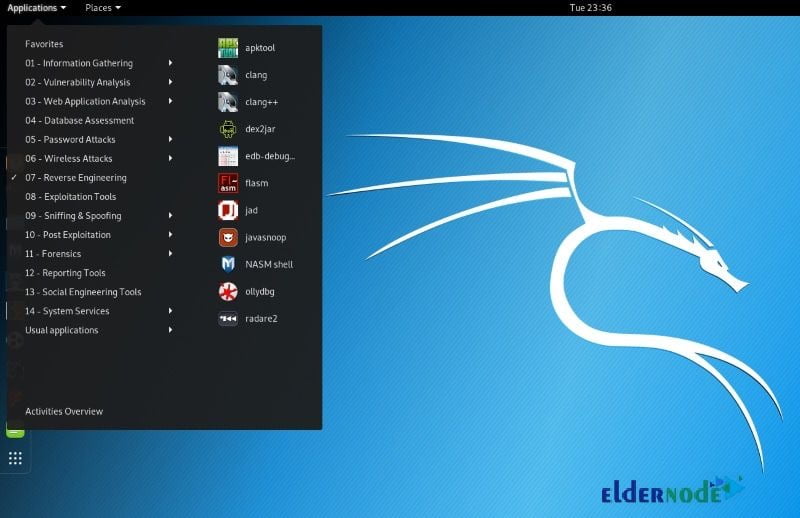
Top 10 tools in Kali Linux Server
1- Aircrack-ng: A tool for intercepting and breaking passwords in wireless communications
2- Burp Suite: A tool to penetrate web-based systems that use the HTTP protocol
3- Wireshark: A tool for analyzing packets in network protocols
4- Sqlmap: A tool for penetration testing through injection of SQL code
5- Owasp Zap: Web-based tools vulnerability detection
6- Metasploit: An environment for coding and hacking tools
7- Nmap: Network search and scan tool and identify all active nodes in the network
8- Maltego: A tool for identifying and collecting data before it can penetrate
9- John the Ripper: A tool for breaking passwords
10- THC Hydra: For Brute Force attacks
In addition to the tools mentioned above, a more complete categorization of the Kali Linux operating system is available below:
Information Gathering: Includes a set of tools for gathering information
Web Application: Includes a suite of tools for penetrating web-based applications
Reporting Tools: Tools for reporting and gathering information
Hardware Hacking: A tool for Android and Arduino hack
Stress Testing: A set of tools for uploading and testing the system load
Reverse Engineering: A set of tools for reverse engineering systems
Sniffing / Spoofing: A suite of tools for detecting and performing impersonation attacks
Exploitation Tools: A tool for executing hack and intrusion codes and Exploit
Wireless Attacks: A set of tools to attack wireless installations and networks
Password Attacks: A tool for breaking passwords
Vulnerability Analysis: System vulnerability analysis and data gathering
Conclusion
In this article, Kali Linux was introduced to you and you learned about its applications. Kali Linux is known as one of the most recommended Linux distributions for ethical hackers. While people think that Kali is a tool for hacking or cracking social accounts or web servers, hackers and webmasters can utilize some of the tools to easily run a scan of your web server or web page.




Great post, really helpful with tons of great insight!